ATIS’ Next G Alliance (NGA) released couple of new reports. The first is 6G Distributed Cloud and Communications System which overviews the distributed cloud and communications system from the perspectives of design goals, driving forces, challenges, research directions and the path to realization. Its intention is to spark research and design discussions to realize the NGA’s audacious goal for distributed cloud and communications system.
The second is Trust, Security and Resilience for 6G Systems which presents five research directions to aid in establishing trust, security and resilience for 6G systems: Security Assurance and Defense, Confidential Computing, Secure Identities and Protocols, Service Availability and Post-Quantum Cryptography. There is an imminent need to eliminate all single points of failure and to architect a network based on zero-trust principles to provide users high levels of reliability along with attention to availability, functional safety and privacy. 6G technologies will accommodate these needs more effectively, even as the industry continues to innovate on standalone 5G systems to meet immediate concerns associated with earlier design choices.
The following is from the 6G Distributed Cloud and Communications System report:
The 6G distributed cloud and communications system is expected to provide communication, computing, and data services. This contrasts with prior generations, which primarily provide communication services. The communication, computing, and data services can be provided in forms of infrastructure service (e.g., containerized communication computing-data infrastructure), platform service (e.g., platform services for scaling out computing across mobile devices and network compute), and software services (e.g., data analytics services). The 6G system needs to be designed with the capability of providing those various forms of services (e.g., Everything as a Service (XaaS)). A computing service plane and a data service plane are expected to be introduced in 6G systems in addition to the communication service plane.
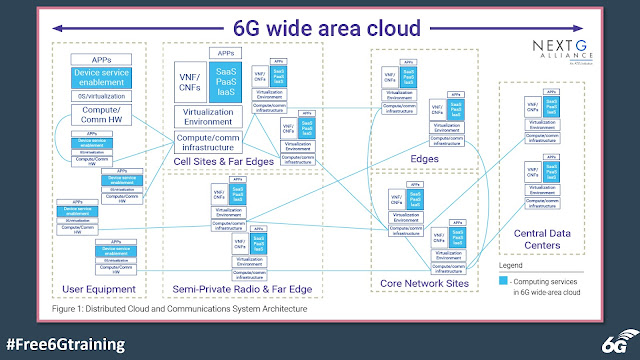
Development of new service subscription models are also foreseen. Subscribers to 6G XaaS are anticipated to include mobile users, mobile device vendors, application providers, cloud-service providers, etc. Figure 1 shows an example of the envisioned 6G distributed cloud and communications system, which includes:
- User equipment with a unique cloud and communications stack.
- Cell sites with far-edge capabilities and a facility cloud and communications stack.
- Semi-private radio sites (e.g., homes, offices, factories, other enterprises) with far-edge capabilities on a facility stack that may home to core sites (possibly more than one), and can potentially operate without connection to the core sites as needed.
- Edge sites with facility stacks.
- Core sites with facility stacks.
- Central data centers with facility stacks extending communication services to the data center end points, thus permitting end-to-end QoS and service feature guarantees.
The following is from Trust, Security, and Resilience for 6G Systems report:
Trustworthiness may be defined as the measure of confidence in the behavior of a person, organization, or technological solution. For mobile communication networks, trust is built up from sentiments gathered from a variety of sources that include geopolitical realities, supply chain reliability, design requirements, standardization of interfaces, technological tools, operational resilience, risk management, and comprehensive test and certification. The technological implications of trustworthiness may be isolated as follows. In the case of engineering systems, including networks, trustworthiness is defined as the confidence in the ability that a system performs as expected in the face of environmental disturbances, impairments, errors, faults, and attacks. This definition of trustworthiness has several proof points specific to the establishment of ICT and pertinent to 6G:
- Business processes and economic value chains are organized in a manner that does not create a lack of confidence in equipment, actors, and processes associated with network services.
- Diligence in developing standards that can be tested and certified for consistency with well-defined requirements.
- Networks and associated services that are secure, privacy-preserving, reliable, available, and resilient.
- Assurance that the network equipment and associated services are interoperable across the ecosystem and that networks are deployed and operated in accordance with the expectations of users.
Figure 1 illustrates the organization of a trustworthy network as a lifecycle that includes a strong assurance of security, privacy, reliability, availability, and functional safety. The entire construct is built on an understanding of the risk and threat landscape that will be addressed by a process that spans development, deployment and management/configuration, and operation of the network or service. The development of the network must exhibit diligence toward trustworthy design through the standardization, design, development, and integration phases. The operational aspects of the trustworthy 6G network will be based on an automated approach to security assurance and defense, and a strong focus on performance management that is customized to the resources available and the use case.
In addition, the network must be resilient to severe disruptions, allowing for predictive analysis and response to threats and disturbances. In what follows, specific research directions toward important objectives are provided as listed in the four focus areas in the figure, adding research on post-quantum cryptographic techniques and quantum computing advances as a separate research priority towards security.
Related Posts:



Comments
Post a Comment